21st Century Psychic Combat Resources
Q: What is Psychic Combat? A: Psychic Combat is the application of military and martial science to the field of Psychic Phenomenon and the subconscious.
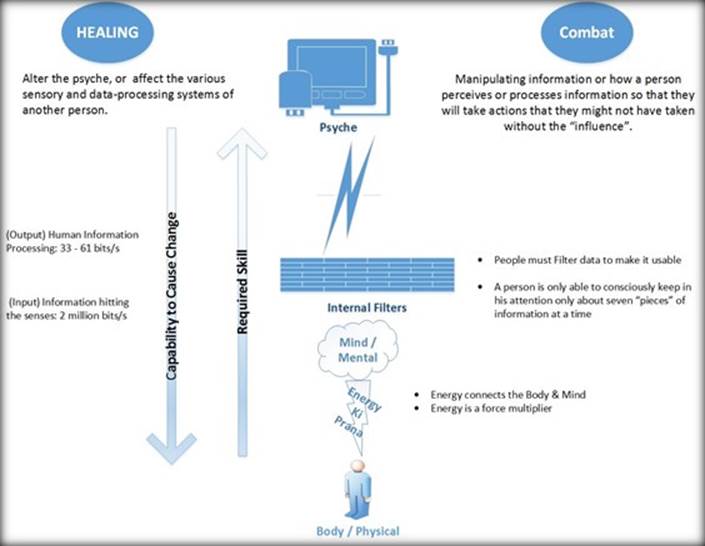
Q: What does Psychic Combat work? A: Psychic Combat is an entirely new arsenal of tools, designed to introduce subliminal messages or to alter the body's psychological and data-processing capabilities, or to incapacitate hostile enemies. These tools aim to control or alter the psyche, or to attack the various sensory and data-processing systems of the human organism. In both cases, the goal is to confuse or destroy the signals that normally keep the body in equilibrium. It can also involve manipulating information or how the enemy perceives or processes information so that they will be compelled to take actions favorable to one's own side.
EXECUTIVE SUMMARY: Psychic Combat focuses on applying military/martial principals and strategies. It is very different from other magical tools such as "hexes", "curses" and "wards" that are vastly more limited in scope and capability. It is based on controlling ones opponents information flow, processing and perception at a subconscious level. Psychic Combat is about "influencing" opponents through the use of subconscious/psychic attacks or to alter the body's psychological and data-processing capabilities. These weapons aim to control or alter the psyche, or to attack the various sensory and data-processing systems of the target with the goal of controlling behavior, perception or incapacitating them.
Psychic based Influence Operations (Psychic Combat) are aimed at achieving specific desired objectives and effects such as changing attitudes, beliefs, or behavior. They have the following characteristics:
• They are directed toward clear specific targets, whether an individual, groups, a population subgroup, or the mass public
• They make use of the most effective combination of information channels that are most likely to reach the targets.
• They are mindful of target characteristics, strengths and weaknesses, attitudes and beliefs that affect a targets willingness to be influenced.
• They are designed to influence targets before they decide or or actually engage in negative behaviors.
• They use information based messages whose content, format, cognitive and emotional appeal, and other characteristics will most resonate with the targets conscious & subconscious.
21st Century Psychic Combat
- Psychological Warfare: A Brief Overview: Psychological warfare is the strategic use of various psychological means to influence a political actor or target audience to maintain or change their thinking, beliefs, or behavior during war. Psychological warfare in the narrow usage is a form of conflict that takes place exclusively during war. Other usages of the term may refer to psychological warfare in much broader contexts including interpersonal relationships, in the workplace, in business, or other social situations. However, the formal use of the term almost always refers to psychological warfare in the context of international conflict and war.
- Protecting Your Mind in These Complex Times - A Neurolinguistic Approach: (NEW) "We are now living in very complex & uncertain times. People are often filled with fear, anger, and deep concern about what’s happening in society and what’s being presented in the media. This workshop will look ways to protect your conscious and subconscious from the ongoing psychic attacks we are exposed to every day. It will give you some tools to help you deal with the stress we all are experiencing. Neuro-Linguistic Programming (NLP) is a model for understanding how people think, behave and communicate. It was originally developed by studying the patterns of communication and thinking to give greater understandings about human behavior and change. It includes methods for learning other people’s attitudes, beliefs and behavior. It’s also the basis of much of Propaganda & "Influence Operations". The Slides are HERE
- The New Geopolitical Space in the Information Era: A Neuroscientific Approach to National Security: Cognitive Warfare, is the interdisciplinary use of technology and an understanding of the brain’s natural processes to influence opinion and behavior. Also known as sharp power, these methods are more technical and accurate than Cold War-age propaganda, and more personal than typical information warfare. With tools like disinformation and big data, outsiders have the ability to exploit vulnerabilities, manipulate belief formation and disseminate a chosen narrative on the grand scale.
- Facebook: Propaganda, Disinformation, Deception & influence Operations - This is a Non-Partisan group focused on understanding the theory & application of Influence Operations. It is NOT about Political discussions or conspiracy theories. Influence operations are focused on affecting the perceptions and behaviors of individuals, groups, or entire populations by impacting a Targets behaviors, emotions, reasoning, perceptions, decision cycle, attitudes, beliefs, values or even memories.
- MODERN PSYCHO-VIRUS WAR OF AI FOR THE GLOBAL MIND:The importance of the information component of the modern synergetic war is underlined and the technologies for Data Mining modelling the media influence on a society are briefly described. Thus, modern civilization has faced new threats of psycho-viral contamination of public consciousness, which in its disastrous social and political consequences can be considered as a weapon of mass destruction, requiring the development of protection methods based on the ethical compromise between the democratic values and the needs of mental Défense. In essence, this is a war of psycho-viruses constructed with help of AI for mastering the virtual reality of the global network mind.
- A COMPUTER AIDED SYNERGETIC WW3!: In a synergetic war, the priority strategy consists in infecting the enemy with provocateurs and psychoviruses to provoke the enemy‟s self-destruction. The most vulnerable foci of the society under attack are located at the points of internal social and political tension and there the external aggressor‟s actions are targeted.
Monitoring the media, including social networks, it is possible to detect a psychovirus attack with destructive memes and thereby predict the physical actions that they stimulate and support.
- The Mind Has No Firewall: An entirely new arsenal of weapons, based on devices designed to introduce subliminal messages or to alter the body's psychological and data-processing capabilities, might be used to incapacitate individuals. These weapons aim to control or alter the psyche, or to attack the various sensory and data-processing systems of the human organism. In both cases, the goal is to confuse or destroy the signals that normally keep the body in equilibrium. This article examines energy-based weapons, psychotronic weapons, and other developments designed to alter the ability of the human body to process stimuli.
- Deploying Mindfulness to Gain Cognitive Advantage: Considerations for Military Effectiveness and Well-being. Mindfulness training (MT) programs aim to promote this mental mode via introduction to specific mindfulness exercises. MT engages and strengthens three key processes. These are: 1) attentional orienting, which is the ability to select and sustain attention on a subset of information while remaining undistracted; 2) meta-awareness, which is the ability to monitor one’s ongoing experience with an awareness of doing so; and 3) decentering, which is the ability to view one’s experience at a psychological distance so that biases, mind-sets, and interpretations are viewed as mental processes rather than accurate depictions of reality.
- Shaping Perceptions: Processes, Advantages, and Limitations of Information Operations: The value of manipulation and influence as part of the greater effort of achieving specific military and non-military goals has long been appreciated. Information operations are but one aspect of national statecraft and seek to influence targeted audiences – like foreign leaders or civilian populations – to gain a competitive military or political edge. Partially rooted in fields like cognitive psychology, electronic and cyber warfare, and operations security, information operations are employed to shape the perceptions of specific targets to ultimately achieve a specific end, thereby influencing their decision-making and behavior.
- Human Network Attacks: It is the security of the data processor known as the mind, which unfortunately has no innate firewall to protect it from either deceptive or electromagnetic processes. As a result, the mind of the soldier on the battlefield is potentially the most exploitable and unprotected IW capability our military possesses. Soldiers vulnerability to human network attacks (HNA) should be an area of close attention for scientists in the early years of the new millennium."In the past half century the potential for working on the consciousness, psyche or morale of a person, society or the composition of an armed force has grown dramatically. One of the main reasons is the considerable success achieved by many countries in their systematic research in the areas of psychology, psychotronics, parapsychology, other new psychophysical phenomenon, bioenergy, biology and psy-choenergy in the fields of security and defense.
- Rethinking Extrasensory Perception: Toward a Multiphasic Model of Precognition: In this article, we define precognition as an atypical perceptual ability that allows the acquisition of non-inferential informationn arising from a future point in spacetime. The Multiphasic Model of Precognition (MMPC) identifies two distinct phases: The first is the physics domain, which addresses the question of retrocausation and how it is possible for information to traverse from one spacetime point to another. We suggest that the solution might be found within entropic considerations. The second is the neuroscience domain, which addresses the acquisition and interpretation of retrocausal signals. We propose that this occurs across three stages: (a) perception of signals from an information carrier, based on psychophysical variability in a putative signal transducer; (b) cortical processing of the signals, mediated by a cortical hyper-associative mechanism; and (c) cognition, mediated by normal cognitive processes, leading to a response based on retrocausal information. The model is comprehensive, brain-based, and provides a new direction for research requiring multidisciplinary expertise.
- REMOTE VIEWING Post 9/11
- Anomalous Human Cognition: A Possible Role within the Crucible of Intelligence Collection: A detailed examination of the documented history of the U.S. RV program strongly suggests that remote viewing could provide high value intelligence capable of assisting the IC in addressing some of the challenges it currently faces.
- Unconventional Human Intelligence Support: Transcendent and Asymmetric Warfare Implications of Remote Viewing: Yet, remote viewing's demonstrated capacity for providing unique, non-technical intelligence support posits said program as a leading candidate for exploring currently evolving forms of warfare. Presented within is a brief history of the remote viewing program, an examination of its evolution over the course of more than twenty-three years, and a discussion of its continuing relevance to national security and emerging warfare trends.
- Evaluating the Use of Remote Viewing in the Global War on Terrorism: This paper will evaluate the potential application of Remote Viewing (RV) techniques to the Global War on Terrorism (GWOT). Specifically it will look at how RV can be used to support intelligence and counterterrorism operations. The paper will rely primarily on declassified government documents on the Stargate program. Stargate was the collective name for advanced psychic functioning or Remote Viewing experiments and programs that were undertaken for twenty years. Its purpose was to create a trainable, repeatable and as much as possible, accurate method of psychic intelligence gathering. By reviewing these documents, this paper will attempt to determine if remote viewing can be a useful tool in fighting modem jihadi terrorists.
- Dec. 26/19 - Astral Travel with Richard Benack
- From Psyops to Neurowar: What Are the Dangers? Current and near future technology will make it possible to not only merely influence the enemy’s mind and behavior, but to actually control it. This paper argues that new methods of influencing the brain and the central nervous system and thereby mental capacity, emotion, and thought could become central to future military strategy and the conduct of war, conflict, and economic competition.
- Influence Operations Resources: Influence operations are focused on affecting the perceptions and behaviors of leaders, groups, or entire populations. Influence operations employ capabilities to affect behaviors, protect operations, communicate commander’s intent, and project accurate information to achieve desired effects across the cognitive domain. These effects should result in differing behavior or a change in the adversary’s decision cycle, which aligns with the commander’s objectives.
- COGNITIVE WARFARE: YOUR MIND IS THE BATTLEFIELD: Influence Operations (IO) GOAL: Influence an adversary or potential adversary (Targets) in support of specific political or policy objectives. This can be done by:
- Integrating Psychology, Cybernetics, Information Theory and Technology into a weapon
- Controlling their Targets information flow, processing, behavior and perception through the use of subconscious attacks
- Undermining their will, cohesion and decision making ability
- Protecting one’s own leaders, decision-makers, population and allies from Influencing attacks
- NEOCORTICAL WARFARE? THE ACME OF SKILL: Neocortical warfare uses language, images and information to assault the mind, hurt morale and change the will. It is prosecuted against our enemies weaknesses or uses our strengths to weaken them in unexpected and imaginative ways. We should devote the weight of effort and more resources to the deliberate and continual pursuit of nonviolent influence over the adversary.
- FOUNDATIONS OF EFFECTIVE INFLUENCE OPERATIONS A FRAMEWORK FOR ENHANCING ARMY CAPABILITIES: Since the end of the Cold War, there has been growing interest in improving the nation’s ability to employ various forms of “soft power” capabilities that might allow the United States to effectively influence the attitudes and behavior of particular foreign audiences while minimizing or avoiding combat entirely. The present study was undertaken to assist the U.S. Army in understanding “influence operations” and to identify approaches, methodologies, models, and tools that may be useful in planning, executing, and assessing influence operations.
- COMMAND DYSFUNCTION: MINDING THE COGNITIVE WAR: One way to visualize the cognitive warfare approach is in a three-category framework. The categories include of the adversary’s command baseline, stressors, and deception. The command baseline represents the adversary’s existing decision making characteristics. It consists of his expectations, perceptions, command arrangements, decision procedures, experience, training, tradition, culture and any other significant factors that constitute his decision making. The baseline includes both strengths and weaknesses. Weaknesses include self-induced problems that affect the accuracy and speed of his decision cycle. The second framework category consists of stressors. “Stressors” come in two sets, physical and psychological. The physical stressors are actions that complicate and degrade the adversary’s decision making by pressuring his capabilities and time resources. The introduction of physical stressors leads to the second kind, those that are psychologically felt in the mind of target. The final framework category is deception. The A-type deception program increases uncertainty by generating a number of alternatives for the adversary to consider. Deception programs work in the opposite direction in terms of uncertainty and seek to convince the victim that he is “right” about the deceiver’s methods and objectives, when he is objectively “wrong.” Both deception types exploit the command baseline’s expectations and perceptions.
- Cognitive Joint Force Entry White Paper: The Joint Publication 3-13, Information Operations, states: "the cognitive dimension encompasses the minds of those who transmit, receive and respond to or act on information. Cognitive Depth is a dimension of the operating environment encompassing a populations' realm of perceptions, beliefs, opinions, and attitudes. It is possible that the perceptions, dispositions, and attitudes of people, groups, and populations can be exposed to a near limitless realm of influence. It also incorporates the dimension of time, past, present, and future. This characteristic requires a capacity to maintain persistent engagement in the information environment, understanding the past and looking into the future.
- THE BIOLOGY OF DISINFORMATION: memes, media viruses, and cultural inoculation: The longest-term strategy to defend against memetic attack, and ultimately the most effective one in our opinion, is to strengthen the social and cultural resiliency of the population under attack. Human beings have evolved complex and adaptive strategies for social cohesion. Our neurology is primed to establish rapport with other humans, to utilize reciprocal altruism, and to work toward common goals. Such social relationships require real-world, organic calibration to take effect. In virtual spaces, these mechanisms cease to function. In fact, when human beings fail to establish “social resonance” through digital media, they tend to blame not the low fidelity of the medium, but the trustworthiness of the other party.
- White Paper on Bio-Psycho-Social Applications to Cognitive Engagement: Information Operations (IO) doctrine defines the cognitive domain as the component of the information environment (IE) that encompasses the gray matter of those who transmit, receive, and act upon information. Cognitive operations such as information processing, perception, judgment, and decision-making are the most vital aspect of the IE. Cognition is influenced by individual and cultural beliefs, norms, vulnerabilities, motivations, emotions, experiences, morals, education, mental health, identities, and ideologies and thus requires research and analysis methods from the bio-psycho-social sciences to understand and manipulate.
- Detection of Propaganda Techniques in News Articles: (NEW) "Propaganda aims at influencing people’s mindset with the purpose of advancing a specific agenda. It can hide in news published by both established and non-established outlets, and, in the Internet era, it has the potential of reaching very large audiences (Muller, 2018; Tardaguila et al., 2018; Glowacki et al., 2018). ´ Propaganda is most successful when it goes unnoticed by the reader, and it often takes some training for people to be able to spot it. The task is way more difficult for inexperienced users, and the volume of text produced on a daily basis makes it difficult for experts to cope with it manually. With the recent interest in “fake news”, the detection of propaganda or highly biased texts has emerged as an active research area. However, most previous work has performed analysis at the document level only or has analyzed the general patterns of online propaganda.
- Countering Information Influence Activities: A Handbook for Communicators: ANATOMY OF AN INFORMATION INFLUENCE CAMPAIGN
- Using influence techniques: Public relations, marketing, diplomacy, opinion journalism, and lobbying are examples of accepted ways of influencing people’s views and behaviours. Information influence activities mimic these forms of engagement but use the techniques deceptively.
- Disrupting public debate: Foreign powers use information activities to influence those fields and debates from which they can benefit. This can be done both directly and indirectly, through everything from open propaganda to covert funding of civil society groups. When illegitimate actors interfere in legitimate public debate it can change society’s perception of leading opinions and influence decision-making.
- Acting in self-interest: Influence activities are intended to achieve specific goals that benefit a foreign power. The objective might be anything from destabilising a society politically, preventing specific decisions from being taken, or polarising a political debate.
- Exploiting vulnerabilities: All societies have their challenges. These may be social or class tensions, inequality, corruption, security issues, or other problems central to social life. Hostile foreign powers identify and systematically exploit these vulnerabilities to achieve their goals.
- COGNITIVE HACKING: (NEW!) Cognitive hackers manipulate a user’s perception and rely on his changed actions to carry out the attack. Effective countermeasures must aim at preventing misinformation through authentication, collaborative filtering, and linguistic analysis.
- Cognitive Hacking: A Battle for the Mind: (NEW!) Cognitive hacking can be either covert, which includes the subtle manipulation of perceptions and the blatant use of misleading information, or overt, which includes defacing or spoofing legitimate forms of communication to influence the user. In covert cognitive hacking, the attacker tries to disguise the attack; in overt hacking, he does not. At times, the distinction between the two categories is not always obvious. For example, some defacements introduce subtle changes that might be considered covert. Some attacks intended to be covert end up being overt because they’re not terribly believable. Overt cognitive hacking, while more prevalent than covert forms, is more of a nuisance and embarrassment than a serious threat. Covert cognitive hacking, on the other hand, is likely to have more significant and less predictable consequences.
- Deception, Lies, and Manipulation in Cyberspace: Critical Thinking as a Cognitive Hacking Countermeasure: (NEW!) Fallacious or misleading information disseminated using technology to deceive, exploit, and manipulate psychological weaknesses, perceptions, and decision-making is identified as disinformation. The exponential growth of the internet and the immense wilderness of information impacts human judgment, perception, and cognitive ability to discern the credible from incredible. The purpose of this literature review is to explore critical thinking as a counter to cognitive hacking and provide a conceptual analysis of fallacy and fallacious appeals as underpinnings to disinformation. The results of this literature review suggest that with bias suspension and awareness of fallacy and fallacious appeals, critical thinking is a viable solution to recognize disinformation. Also, future research may involve qualitative and quantitative studies on disinformation and the impacts on societal reality, decision-making, and the existence of truth.
- DERADICALIZATION
- The Journal for Deradicalization (JD) is the only independent and peer reviewed open access online journal about the theory and practice of deradicalization and processes of radicalization worldwide. The JD is published four times per year (quarterly). The JD seeks to provide a unique platform for established scholars as well as academics, policy makers and professionals entering the field of Terrorism, Political Violence, Conflict Studies, and (De-) Radicalization research.
- Toward a Constructivist Model of Radicalization and Deradicalization: A Conceptual and Methodological Proposal: This article identifies common features of existing models of radicalization and deradicalization, such as the transition from uncertainty to certainty, before integrating these in a model based upon personal construct theory. It is proposed that the personal construct concepts of validation and invalidation are particularly relevant to processes of identity change such as radicalization and deradicalization. Thus, it is argued that radicalization occurs when major invalidation of an individual’s construing is followed by the development of a new radicalized view of the world that provides a turning point in his or her sense of identity and a more structured and certain view of the world. There is likely to be seeking out of validation for this view in interactions with others who share similar views or by extorting evidence for the individual’s radical constructions. These constructions are likely to involve extreme negative views of another group, by contrast to members of which, and possibly by taking extreme action against this group, the individual’s new self-construction may become further defined. These same processes can be seen to operate in deradicalization, and it will therefore be argued that the model has implications for the development of deradicalization programs.
- The anatomy of undue influence used by terrorist cults and traffickers to induce helplessness and trauma, so creating false identities (NEW) : There is a need to update the legal system to recognize the use of hypnosis and undue influence occurring throughout the world. Extremist groups are deceptively recruiting and indoctrinating people to do terrorist attacks. Human traffickers are grooming and using hypnosis and social influence techniques to create labor and sex slaves. In this paper, a number of key concepts and models will be used to more fully define DSM-5's Dissociative Disorder 300.15: Festinger's Cognitive Dissonance Theory, along with Robert Jay Lifton and Margaret Singer's work (1995) are the foundation of the BITE model of mind control (Hassan, 1988). Behavior, Information, Thought, and Emotional Control are the four overlapping components through which destructive groups bring people to be obedient and compliant to authority. A programmed cult identity is created through a complex social influence process. That false identity dominates real identity. The ethics and morality of undue influence are understood differently. In this paper, we analyze the techniques of breaking down the existing personality and creating a false or pseudo-identity. The Influence Continuum and BITE mind control model and Lifton's eight criteria for Thought Reform are discussed; Scheflin's Social Influence Model (2015) is presented as one tool for analyzing undue influence in a forensic and juridical context.
- REFLEXIVE CONTROL
- Russia’s Reflexive Control Theory and the Military: One of the prime goals for a commander in warfare is to interfere with the decision-making process of an enemy commander. For Russia, one of the primary methods is through the use of the theory of reflexive control (RC).This principle can be used against either human-mental or computer-based decision-making processors. Reflexive control is defined as a means of conveying to a partner or an opponent specially prepared information to incline him to voluntarily make the predetermined decision desired by the initiator of the action.
- The Soviet Theory of Reflexive Control in Historical and Psychocultural Perspective: This new method is the Soviet theory of reflexive control, which, briefly stated, can be defined as, "a means of conveying to a partner or an opponent specially prepared information to incline him to voluntarily make the predetermined decision."
- Russian Information-Psychological Actions: Implications for U.S. PSYOP: Another nontraditional information-psychological action is the Russian concept of reflexive control, a "branch of the theory of control related to influencing the decisions of others. In a military context, it can be viewed as a means for providing a military commander with the ability to indirectly maintain control over his opponent commander's decision process." Reflexive control is the process of manipulating information so that one's enemy will be compelled to take actions favorable to one's own side. It can include "Conducting psycho-energetic warfare and other types of nontraditional influence on the consciousness and the mental state of the enemy.
- REFLEXIVE CONTROL BY DESIGN: CRAFTING EMERGENT OPPORTUNITY IN COMPLEX SYSTEMS: By communicating ideas that create or confirm another’s assumptions, an actor can shape the environment by imposing a dilemma, provoking another to act in a desired manner. Conversely, by confounding another’s assumptions, an actor can disrupt the other’s decision-making process. Finally, by creating perception of an unanticipated threat or opportunity, an actor can force another to analyze hastily emerging observations designed to trigger specific assumptions reflexively. Figure 1, below, offers a way of visualizing this relation of assumptions and risk calculus into a usable framework to employ and defend against reflexive control.
- COGNITIVE BIASES AND REFLEXIVE CONTROL: One modern tactic, particularly used by the Russian government, is called reflexive control. This hybrid warfare tactic is used to manipulate an opponent into unknowingly making decisions benefiting the manipulator while harming the opponent. Though executed through many outlets, reflexive control is aimed at flaws within the opponent’s decision making process. Many such flaws are categorized as cognitive biases derived from mental shortcuts that can lead the brain to misjudge information
- On Cyber-Enabled Information/Influence Warfare and Manipulation: Information/influence warfare and manipulation (IIWAM) is the deliberate use of information by one party on an adversary to confuse, mislead, and ultimately to influence the choices and decisions that the adversary makes. IIWAM mostly uses words and images to persuade, inform, mislead, and deceive so that the adversary does not use the (fully operational) military assets it does have, and the military outcome is the same as if those military assets had been destroyed. The targets of IIWAM are the adversary’s perceptions, which reside in the cognitive dimension of the information environment. IIWAM focuses on damaging knowledge, truth, and confidence, rather than physical or digital artifacts; the former reside in “brain-space” rather than 3-D space or cyberspace. IIWAM seeks to inject fear, anger, anxiety, uncertainty, and doubt into the adversary’s decision making processes. Successful IIWAM practitioners alter adversary perceptions and are able to predict how altered perceptions increase the likelihood that the adversary will make choices that are favourable to the IIWAM practitioner.
- Nine Links in the Chain: The Weaponized Narrative, Sun Tzu, and the Essence of War: The weaponized narrative targets our minds, which usually lack the resistance our bodies enjoy. We have no immune system for the mind. Defending the body but sacrificing the will still means defeat. The weaponized narrative is distinct from traditional information attacks like disinformation or propaganda because several factors, from cognitive neuroscience to communications technology, are now combining in unexpected, synergistic ways. Six key differences (abbreviated V3S3) are Vector, Vulnerability, and Virulence; Scope, Speed, and Synergy.
- Information Operations: The Hard Reality of Soft Power Probably the most interesting and neglected Russian element by Westerners is the information-psychological component of IO. The Russian military excels in the study of these areas especially over Western theorists. The Russia military scientists have been studying not only the ability of information warfare to affect the values, emotions, and beliefs of target audiences (traditional psychological warfare theory), but also methods to affect the objective reasoning process of soldiers. That is, Russia is interested in ascertaining how to affect not only the data-processing capability of hardware and software but also the data-processing capability of the human mind. Other less known but reported information-psychological related activities include:
• Military unit 10003, which studies the occult and mysticism, reportedly to understand the recruiting and “brain washing” techniques of these groups
• Anti-ESP training in the strategic rocket forces, designed to enable missile launchers to establish mental firewalls in case someone from the outside attempts to take over their thoughts
• Astrologers in the Ministry of Defense, who predict ambushes, plane crashes, and other phenomenon
• Practice with the “25th frame effect,” which tries to insert a subliminal message into every 25th frame of a movie or computer generated scene
• Applying electromagnetic impulses to the head of a soldier to adjust his/her psychophysical data
• Remote viewing and psychotronics
- SOMATIC SCIENCE
- Exploratory Studies of External Qi in China: Scientists have long been interested in measuring external qi (wai qi), or the out-of-body biofield effect, during qigong healing and have produced a large body of literature in this area during the past two decades. This paper briefly reviews five different categories of major studies on external Qi (EQ) that were performed in China: physical detectors, chemical dynamics methods, biological detectors, life-sensors detectors, and detectors using human body.
- RESEARCH INTO PARANORMAL ABILITY TO BREAK THROUGH SPATIAL BARRIERS: This article uses strict scientific procedures, one of a kind test samples, videotape and high speed photography to demonstrate the objective existence of the paranormal ability of breaking through spatial barriers.
- Neuro-Linguistic Programming (NLP): Influence and Information Gathering
- Analysis of Success of Mobilization to Terror using Tools of Neuro-Linguistic Programming (NLP): The current research is dedicated to put forward the ways the Internet surfers are mobilized for the aims of illegal and harmful actions and even terror. We introduced usage of a psychological-linguistic approach known as NLP (Neuro-Linguistic Programming) which constructs new realities and a fast shift in the behavior of the treated subjects after the beginning of the exposure. This approach is not accepted widely in academic circles yet its tools are frequently used by security forces for interrogations, hostages incidents and evidences collection. In the recent years the data on mobilization for illegal actions and even for terror intends continues to grow and this article is our modest attempt to shed a light and to simulate and analyze the content environment of the surfers exposed to the substance of the sites propagating terror.
- SYMBIOTIC RADICALISATION STRATEGIES: PROPAGANDA TOOLS AND NEURO LINGUISTIC PROGRAMMING: (NEW!) The rise of Islamic State has seen a rise in the threat and incidences of domestic terrorism. Sophisticated strategies are being used to target youth and draw them into the ideology of Islamic state and other terrorist groups. Two common strategies used by Islamic State are the use of propaganda tools as well as Neuro linguistic programming strategies. This paper looks at how these strategies were used through a longitudinal online ethnographic study on the social media site Facebook. Data collected revealed that these two strategies were used in a targeted manner and worked together in a symbiotic fashion to create a change in the mental frameworks of an individual. Both strategies worked in the linguistic domain to help shape and internalise key discourses and ideologies. Finally, these strategies were used implicitly without any direct references on how ton achieve change.
- Social Engineering:The Art of Human Hacking: NLP is how to use the language of the mind to consistently achieve, modify and alter our specific and desired outcomes (or that of a target). Neuro-Linguistic Hacking (NLH) NLH is a combination of the use of key parts of neuro-lingusitic programming, the functionality of microexpressions, body language, gestures and blend it all together to understand how to “hack” the human infrastructure.
- Symbiotic Radicalisation Strategies: Propaganda Tools and Neuro Linguistic Programming: The rise of Islamic State has seen a rise in the threat and incidences of domestic terrorism. Sophisticated strategies are being used to target youth and draw them into the ideology of Islamic state and other terrorist groups. Two common strategies used by Islamic State are the use of propaganda tools as well as Neuro linguistic programming strategies. This paper looks at how these strategies were used through a longitudinal online ethnographic study on the social media site Facebook. Data collected revealed that these two strategies were used in a targeted manner and worked together in a symbiotic fashion to create a change in the mental frameworks of an individual. Both strategies worked in the linguistic domain to help shape and internalise key discourses and ideologies. Finally, these strategies were used implicitly without any direct references on how to achieve change.
- APPLICATION OF NEURO-LINGUISTIC PROGRAMMING TECHNIQUES TO ENHANCE THE MOTIVATION OF AT-RISK STUDENT: "This study has proven the application of Neuro-Linguistic Programming (NLP) is effective in increasing the intrinsic motivation of high-risk students in prison. Intrinsic motivation is addressed in this study covers aspects of self-confidence,desire for change, a passion for learning and perspective on life after independent. The experimental study of pre-and post qualitative approach was performed by using interviews and pre-and post-treatment observation. Selected treatment is a technique derived from the application of NLP techniques consisting of Peace Progressive Techniques (Progressive Relaxation Technique), Exploring the Value of Your Real Techniques (Discover Your True Values Technique) and Technical Excellence Circle (Circle of Excellence Technique). All three techniques are carried out in sequence and findings related to each other. The result is expressed in terms of analysis and transcription were able to answer three main research questions."
- Reid Interrogation Training: The Reid Technique consists of a three-phase process beginning with Fact Analysis, followed by the Behavior Analysis Interview (a non-accusatory interview designed to develop investigative and behavioral information), followed when appropriate by the Reid Nine Steps of Interrogation. In the Reid Technique, interrogation is an accusatory process in which the investigator tells the suspect that there is no doubt as to his or her guilt. The interrogation is in the form of a monologue presented by the investigator rather than a question and answer format. The demeanor of the investigator during the course of an interrogation is ideally understanding, patient, and non-demeaning. The Reid technique user's goal is to make the suspect gradually more comfortable with confessing. This is accomplished by the investigators' first imagining and then offering the suspect various psychological constructs as justification for their behavior.
- Interrogation: Science and Art Foundations for the Future: Few empirical studies in the social and behavioral sciences directly address the effectiveness of interrogation in general, or of specific techniques, in producing accurate and useful information. This paper summarizes existing theoretical and empirical findings and analyzes them in the framework of five topics: models for educing information, strategies to increase the willingness to provide information, strategies to overcome resistance, factors affecting the accuracy of educed information, and the effect of “stress and duress” techniques on obtaining information. A promising body of social science research on persuasion and interpersonal influence could provide a foundation for a more effective approach to educing information in intelligence-gathering contexts.
- Creating Irresistible Influence with NLP: You will learn how to influence more effectively and obtain more of what you really want. In Creating Irresistible Influence with NLP, you'll learn:
- * The crucial difference between influence and manipulation.
* How to hear (and see) what people really want.
* How to increase your influence through a Value Matrix.
* Five ways every one of us makes something more meaningful.
* The importance of Identity Values over Utility Values.
* The five levels of the Pyramid of Influence.
* How everyday metaphors shape our identities and businesses.
* The Five Life Purposes that drive all of us.
* How the stories we tell about ourselves lead to our futures.
- NLP Resources 1:
- SAMPLE PSI RESEARCH PUBLICATIONS: This is a selected list of downloadable peer-reviewed journal articles about psi (psychic) phenomena, most published in the 21st century. There are also some papers of historical interest and other resources.
- Working Psychology Resources: Working Psychology works with social influence: the modern, scientific study of persuasion, compliance, propaganda, "brainwashing," and the ethics that surround these issues. Since World War II, social influence has become a vastly expanding field of study devoted to discovering the principles that determine our beliefs, create our attitudes, and move us to action.
- Feeling the Future: Experimental Evidence for Anomalous Retroactive Influences on Cognition and Affect: "The term psi denotes anomalous processes of information or energy transfer that are currently unexplained in terms of known physical or biological mechanisms. Two variants of psi are precognition (conscious cognitive awareness) and premonition (affective apprehension) of a future event that could not otherwise be anticipated through any known inferential process. Precognition and premonition are themselves special cases of a more general phenomenon: the anomalous retroactive influence of some future event on an individual’s current responses, whether those responses are conscious or nonconscious, cognitive or affective. This article reports 9 experiments, involving more than 1,000 participants, that test for retroactive influence by “timereversing” well-established psychological effects so that the individual’s responses are obtained before the putatively causal stimulus events occur.
- AN ASSESSMENT OF THE EVIDENCE FOR PSYCHIC FUNCTIONING: Examines research on psychic functioning (PSF) conducted over 2 decades, to determine whether the phenomenon has been scientifically established. Focus was on government-sponsored research conducted at Stanford Research Institute (SRI) and at Science Applications International Corporation (SAIC). Using standards applied to other areas of science, it is concluded that PSF has been well established. The statistical results of the studies examined are beyond what is expected by chance. Effects of a magnitude similar to those found in research at SRI and SAIC have been replicated at laboratories around the world. The magnitude of PSF exhibited is reliable enough to be replicated in properly conducted experiments, with sufficient trials to achieve the long-run statistical results needed for replicability.
- NEURINT could be used to (1) enable strategic and/or tactical engagement with, or manipulation of individuals’ or groups’ psychological state(s); (2) provide insights for development of counternarratives that exert maximal effect upon target individuals’ and groups’ neuro-cognitive processes; and/or (3) develop information and/or cyber-based approaches to influencing content and effect(s) of various forms of messaging used by target individuals and groups (e.g.- social media, etc.).
- White Paper on Bio-Psycho-Social Applications to Cognitive Engagement - Information Operations (IO) doctrine defines the cognitive domain as the component of the information environment (IE) that encompasses the gray matter of those who transmit, receive, and act upon information. Cognitive engagement entails understanding the individual nodes with the human domain as such and developing appropriate methods for interacting with them. To paraphrase Sir Basil Henry Liddell Hart, targeting the mind of the enemy commander is more important than the bodies of his troop
- TUTORIAL: MILITARY MEMETICS: Military Memetics is the application of memes for national security. It is a subset of Neuro-Cognitive Warfare. It can provide a coherent, scientific approach for information operations, psychological warfare, and the general war against terrorists. It can prevent or mitigate irrational conflict, reduce the probability of war or defeat, and increase the probability of peace or victory.
-
Sensemaking: Understanding complex, ambiguous environments: Sensemaking is actively working to comprehend the connections among people, places, and events to understand the "big picture". Sensemaking is the "motivated, continuous effort to understand connections (which can be among people, places, and events) in order to anticipate their trajectories and act effectively." It is an activity that depends on extracting environmental cues, interpreting their meaning, and then connecting them in a plausible story.
-
A Tradecraft Primer: Structured Analytic Techniques for Improving Intelligence Analysis: A tool for making oneself more resistant to Influence Operations: This primer highlights structured analytic techniques—some widely used in the private sector and academia, some unique to the intelligence profession. It is not a comprehensive overview of how intelligence officers conduct analysis. Rather, the primer highlights how structured analytic techniques can help one challenge judgments, identify mental mindsets, stimulate creativity, and manage uncertainty. In short, incorporating regular use of techniques such as these can enable one to structure thinking for wrestling with difficult questions.
-
The Conspiracy Theory Handbook: Prebunking: If people are preemptively made aware that they might be misled, they can develop resilience to conspiratorial messages. This process is known as inoculation or prebunking. There are two elements to an inoculation: an explicit warning of an impending threat of being misled, and refutation of the misinformation’s arguments. Prebunkings of antivaccination conspiracy theories have been found to be more effective than debunking.
-
Collaborative Models for Understanding Influence Operations: Lessons From Defense Research: Social media has proven itself an essential tool for catalyzing political activism and social change in the United States and around the world.1 Yet the very features that make it so useful to those seeking to advance the greater good—scalability, mobility, and low costs to entry—also make it prone to manipulation by malign actors who use it to perform influence operations and spread divisive rhetoric. These bad actors looking to sway public opinion include both fringe groups and well-funded, highly staffed government institutions, and they have been prolific in recent years.2 This new type of statecraft is but one example of the wide-ranging impacts social media have on society, a topic that demands greater research and long-term institutional investments.
- Psychic Combat Presentation - A detailed overview of Offensive and Defensive Psychic Combat and how to use it. The Word Document has the link to the Presentation. PW Protected
20th Century Psychic Combat
- The First Earth Battalion Handbook: The First Earth Battalion was the name proposed by Lieutenant Colonel Jim Channon, a U.S. soldier who had served in Vietnam, for his idea of a new military of supersoldiers to be organized along New Age lines. Channon envisioned that the First Earth Battalion would organize itself informally: uniforms without uniformity, structure without status, and unity powered by diversity, and members would be multicultural, with each race contributing to "rainbow power".[4] He also proposed as a guiding principle that members of the First Earth Battalion seek nondestructive methods of conflict resolution because their first loyalty is to the planet.
- "The New Mental Battlefield: Beam Me Up, Spock.": PSYCHOTRONICS may be described as the interaction of mind and matter.Two subdivisions of this field have also been investigated. Mind-altering techniques designed to impact on an opponent are well-advanced.The procedures employed include manipulation of human behavior through use of psychological weapons effecting sight, sound, smell, temperature, electromagnetic energy or sensory deprivation.The other area of experimentation involves parapsychological phenomena known as the out-of-body experience (OOBE), remote viewing, extrasensory perception or bioinformation, depending on the source and technique employed. It has been demonstrated that certain persons appear to have the ability to mentally retrieve data from afar while physically remaining in a secure location.
- PSYCHIC WARFARE: EXPLORING THE MIND FRONTIER: Man's greatest potential remains a prisoner of man. Vast untapped mental capabilities create an entirely new battlefield dimension which, if ignored, pose a threat to self and country more serious than nuclear weapons. This threat starts from within. Our fears and cynical attitudes towards psychic capabilities make us our own worst enemies. The Soviets, on the other hand, take psychic research very seriously at all levels, particularly for its military application. Exploring the mind frontier is essential and the key to successful exploration is a greater psychic awareness. The mind is rich in unfathomed resources ripe for exploration, a limitless source of treasures for advancing all mankind, and a serious threat to those who ignore its potential. We must overcome our psychic inhibitions, stop denying the existence of paranormal events, and start trying instead to understand the nature of these phenomena.
- The CIA Star Gate Remote Viewng program; Project Star gate is the collective name for advanced psychic functioning or Remote viewing experiments and programs that were undertaken for over twenty years to create a trainable, repeatable, operational and if at all possible, accurate method of psychic spying or information gathering for the U.S. Military and intelligence agencies (CIA, NSA, DIA).
- Psychic Spies, Acid Guinea Pigs, New Age Soldiers: the True Men Who Stare at Goats: More of this Movie is more true than you would believe,” we’re told, just a few minutes into the movie version of The Men Who Stare At Goats, which opens today. But how many of the film’s outlandish military research projects really happened? Turns out there’s plenty of material in the movie which sticks quite close to the truth — though reality is a bit more complicated.
- OODA Loop: The phrase OODA loop refers to the decision cycle of observe, orient, decide, and act, developed by military strategist and USAF Colonel John Boyd. Boyd applied the concept to the combat operations process, often at the strategic level in military operations. It is now also often applied to understand commercial operations and learning processes. The approach favors agility over raw power in dealing with human opponents in any endeavor.
- MANIPULATING THE OODA LOOP: THE OVERLOOKED ROLE OF INFORMATION RESOURCE MANAGEMENT IN INFORMATION WARFARE. Achieving information superiority through the availability and use of the right information, at the right place, at the right time, to all decision makers, while denying that information to the enemy.
- Living With Fog and Friction: The Fallacy of Information Superiority: Information Superiority - The operational advantage derived from the ability to collect, process, and disseminate an uninterrupted flow of information while exploiting or denying an adversary’s ability to do the same. Getting inside the opponent’s OODA loop is merely a metaphor for being able to act appropriately in response to often-chaotic conditions — otherwise known as being able to gain and maintain the initiative. The objective is to either exploit or create an asymmetry that favors your side. Getting inside the adversary’s decision loop has very little to do with the speed of your decisions and has everything to do with generating effects that the enemy has difficulty reacting to.
- PSYCHOLOGICAL OPERATIONS (PSYOP)
- Psychological Operations: PsyOp is basically the use of communication to influence behavior. It is used against adversaries, their supporters, and their potential supporters. It is defined by the US Army in the following way: “Psychological operations are planned operations to convey selected information and indicators to foreign audiences to influence their emotions, motives, objective reasoning, and ultimately the behavior of foreign governments, organizations, groups, and individuals.” Neocortical warfare is RAND’s version of PsyOp that controls the behavior of the enemy without physically harming them. RAND describes the neocortical system as consciousness, perception, and will. Neocortical warfare regulates the enemy’s neocortical system by interfering with their continuous cycle of observation, orientation, decision, and action. It presents the enemy with perceptions, sensory, and cognitive data designed to result in a narrow set of conclusions, and ultimately actions.
- Future Prospects of Information Warfare and Particularly Psychological Operations: The cognitive domain relates to knowledge acquired through thought, experience and the senses, resulting in a perception, sensation or intuition. It is also the place where understanding, beliefs, norms and values reside and where decisions are made. For the military, this is the domain of intangibles: leadership, morale, unit cohesion, level of training, experience, degree of situational awareness and public opinion. Note that all the contents within the cognitive domain have passed through a filter labelled human perception. This filter consists of the individual’s world view, the body of personal knowledge the individual brings to the situation, his experience, training, values and capabilities (e.g. intelligence, personal style, perceptual acuity, etc.). Since these perceptual filters are unique to each individual, individual cognition is also unique. PsyOps refer to the same techniques of influencing the minds of the people. This power has hard and soft aspects. The hard aspect relates to creating in the minds of people negative perceptions of their state, government, society, etc. in order to sow seeds of alienation. The soft aspect refers to projecting before the targeted audience attractive images of the state or group directing the operation in order to create a desire to follow its lead. Both these aspects have the ultimate objective of subverting the mind of the audience and influencing it to act unconsciously as desired by the state or group directing the operation party to try to mislead the deceiver.
- PSYOP Regimental Blog: (NEW) Authoritative source of information on Psychological Operations (PSYOP) or as it is now called Military Information Support Operations (MISO). Written by a retired senior Army Officer and former Honorary Colonel of the PSYOP Regiment.
- Links to PSYOP Resources
Older Psychic Combat
- The Art of War: The Art of War is an ancient Chinese military treatise dating from the 5th century BC. Attributed to the ancient Chinese military strategist Sun Wu, the text is composed of 13 chapters, each of which is devoted to one aspect of warfare. It is commonly thought of as a definitive work on military strategy and tactics. It was placed at the head of China's Seven Military Classics upon the collection's creation in 1080 by Emperor Shenzong of Song, and has long been the most influential strategy text in East Asia. It has had an influence on Eastern and Western military thinking, business tactics, legal strategy and beyond. Can be used to apply magic in a fighting situation.
- GO RIN NO SHO: A BOOK OF FIVE RINGS: The Book of Five Rings is a text on kenjutsu and the martial arts in general, written by the swordsman Miyamoto Musashi circa 1645.Musashi establishes a "no-nonsense" theme throughout the text. For instance, he repeatedly remarks that technical flourishes are excessive, and contrasts worrying about such things with the principle that all technique is simply a method of cutting down one's opponent. He also continually makes the point that the understandings expressed in the book are important for combat on any scale, whether a one-on-one duel or a massive battle. Descriptions of principles are often followed by admonitions to "investigate this thoroughly" through practice rather than trying to learn them by merely reading. Can be used to apply magic in a fighting situation.
- PSYCHIC SELF-DEFENSE (Dion Fortune): "I am of the opinion that psychic attacks are far commoner than is generally realised, even by occultists themselves. Certainly the general public has no conception at all of the sort of things that are done by people who have a knowledge of the powers of the human mind and set to work to exploit them. I am convinced that this factor played a large part in the witch-cult, and was the real cause of the universal horror and detestation of the witch. These powers have always been known to students of occultism, but nowadays they are known and used by people who would be exceedingly surprised to find who are their fellow-practitioners. Mrs. Eddy, the founder of Christian Science, stumbled on to these methods empirically without ever acquiring any rational knowledge as to their modus operandi. She endeavoured to teach them in such a way that they could only be used for good and their power for evil should be concealed; but that she herself was well aware of their possibilities if abused is witnessed by the dread of what she called "Malicious Animal Magnetism," which shadowed her whole life."
Magic for Enhanced Human Performance
- PSYCHIC SELF DEFENSE I: Assessing Your Own Vulnerabilities: A Tool for identifying your vulnerability to Psychic Attacks
- Boyd’s Real OODA Loop and Fencing: The fencer should seek to manipulate the opponent’s information uptake and not just go through movement and countermovement. The real goal should be to modify the entropy in the fencing environment to one’s advantage. This meant that the fencer seeks to ramp up the opponent’s entropy so that it is higher than one’s own. This was done by adopting an information model of the fencing environment. In this paradigm the fencers are seen as part of a communication system that involves the transmission and reception of fencing movements. This allows one to use the idea of entropy. In information theory entropy is a measure of how much information one needs to resolve the uncertainty in a given message.
- DARPA Improving Warfighter Information Intake Under Stress— Augmented Cognition: One example of this new research is a program now known as the Improving Warfighter Information Intake Under Stress Program. Part of its purposes is to gain battlefield information superiority the enhancement of a single operator’s capabilities such that he or she could carry out the functions of three or more individuals. This belief that information superiority could be achieved by enhancing an operator’s cognitive abilities, Based on the concept of managing cognitive workload through neural and physiological feedback. It’s been long recognized that the information-processing capacity of humans has quickly become a limiting factor in human–computer interactions. This problem has spurred the development of a new scientific discipline called Augmented Cognition (AugCog). Addressing methods for detecting and mitigating limitations of human information processing and designing solutions to enhance exchanging and using information.
- Systema: Principles of the Russian System: When practicing Systema, visualize yourself as a contiguous energy field. In other words, there is no separation of body from mind. Visualize your partner the same way and, as you begin to work, keep this awareness. Don’t contest, don’t try to do, just be moved. If you have truly understood the return energy drills the solutions will come of themselves. If we relax and “listen”, the solution will become apparent and all we have to do is implement it. However, if we already have a technique that we want to use to solve this problem we have limited our ability to perceive the most efficient solution.
- FLOW: The Psychology of Optimal Experience: In positive psychology, flow, also known as the zone, is the mental state of operation in which a person performing an activity is fully immersed in a feeling of energized focus, full involvement, and enjoyment in the process of the activity. In essence, flow is characterized by complete absorption in what one does. According to Csikszentmihályi, flow is completely focused motivation. It is a single-minded immersion and represents perhaps the ultimate experience in harnessing the emotions in the service of performing and learning. In flow, the emotions are not just contained and channeled, but positive, energized, and aligned with the task at hand. The hallmark of flow is a feeling of spontaneous joy, even rapture, while performing a task, although flow is also described as a deep focus on nothing but the activity – not even oneself or one's emotions.
- The Rise of Superman: Decoding the Science of Ultimate Human Performance: It’s a book about a mental state called “the flow” and how adventure and extreme athletes have used it to make tremendous strides in their sports. The characteristics of the flow include extreme focus, time dilation / time distortion, a vanishing sense of self, extremely high performance, fearlessness, and a falling away of everything non-essential to the task at hand.
- Using Behavioral Indicators to Help Detect Potential Violent Acts: Our study focused on the science base for using new or nontraditional technologies and methods to observe behaviors and how the data gathered from doing so might—especially when used with other information—help detect potential violent attacks.
- 3 Effective Techniques to Train Your Situational Awareness and Recognize Change: Awareness is a choice. One has to choose to pay attention. But once that choice is made, the part of the brain responsible for monitoring the senses, known as the Reticular Activating System (RAS) takes over. It switches filters on and off that will fulfill your subconscious desire to pay attention. By simply telling yourself to pay attention to certain things, the RAS will scan for and acknowledge those things when it encounters them.
Being able to develop awareness is dependent upon first knowing the baseline for the area you are in and recognizing any variations to the baseline. These changes in baseline are learned from observation. One must know the baseline. One must recognize disturbances to the baseline and one must recognize if those disturbances represent a specific threat or opportunity.
- Improving Real-Time ESP by Suppressing the Futures: This document details the discovery that individuals successfully using telepathy to perceive real time targets are simultaneously and unknowingly using precognitive ESP to suppress their perception of future targets.
- Predicting the unpredictable: critical analysis and practical implications of predictive anticipatory activity: A recent meta-analysis of experiments from seven independent laboratories (n = 26) indicates that the human body can apparently detect randomly delivered stimuli occurring 1–10 s in the future (Mossbridge et al., 2012). The key observation in these studies is that human physiology appears to be able to distinguish between unpredictable dichotomous future stimuli, such as emotional vs. neutral images or sound vs. silence. This phenomenon has been called presentiment (as in “feeling the future”). In this paper we call it predictive anticipatory activity (PAA). The phenomenon is “predictive” because it can distinguish between upcoming stimuli; it is “anticipatory” because the physiological changes occur before a future event; and it is an “activity” because it involves changes in the cardiopulmonary, skin, and/or nervous systems. PAA is an unconscious phenomenon that seems to be a time-reversed reflection of the usual physiological response to a stimulus. It appears to resemble precognition (consciously knowing something is going to happen before it does), but PAA specifically refers to unconscious physiological reactions as opposed to conscious premonitions.

FIGURE 1 - Psychic Combat Targets


Sword Circle Training Materials
Home






